When you connect devices to Onomondo’s cellular IoT network, you’re not only gaining global coverage, you also have a tonne of other benefits such as a powerful management platform, a public API, PAYG data pricing, and no-code cloud integration.
Another area we really excel in is the ability to offer deep network insights for all devices no matter where they are in the world. This article explores our Network Logs insights tool and offers examples on it’s use when debugging IoT devices.
Table of Contents
What are Network Logs?
Network Logs has helped hundreds of IoT business get quick and valuable insights on the connectivity status of their IoT and M2M devices.
Network Logs show you which networks your devices authenticate with and attach to, including which technology was used. Most commonly you will see:
- 2G (Also known as GPRS/Edge)
- 3G (Also known as UMTS)
- 4G (also known as LTE and currently also includes most LTE-M connections)
- NB-IoT
- LTE-M (separation of LTE-M from LTE signalling happened in later releases of the standards, and is still not common)
In LTE, you will often also see two components of an attachment:
- The network registration shown as
attached 4G connection, which is the same as seeing+CEREG: 5when using the AT Command AT+CEREG?. - Data session creation shown as
attached data connectionand this is the same as activating the APN context.
Seeing network insights in real-time and globally dramatically streamlines troubleshooting.
We believe transparency is key, which is why Onomondo provides all information from the RAN to Core Network for your use.
Watch our brief tech talk on Network Logs to find out more.
A GSM example
The device will start attaching to our network by requesting permission. It is at this stage that the network list is checked, as well as other features like if there is an IMEI lock. This will appear as allowed or not allowed as well as the reason it was denied.
For example, if the network is on your network list in Onomondo (aka network allow list or network whitelist), the device receives the response that it is allowed to attach. Conversely, if the network is not on your network list, then the connection will be denied.
Additionally, if a device fails to authenticate with a network, Network Logs will show the reason for that.
Here’s an example of a denied connection on GSM.

An attached data connection example
This is when the device has successfully created a connection to the internet through Onomondo’s Core and can start sending data. This is also when a device is considered “online”.
Depending on the technology, this step can have different names, such as “PDP context activation” in 2G/3G and “APN” or “Session activation” in LTE.
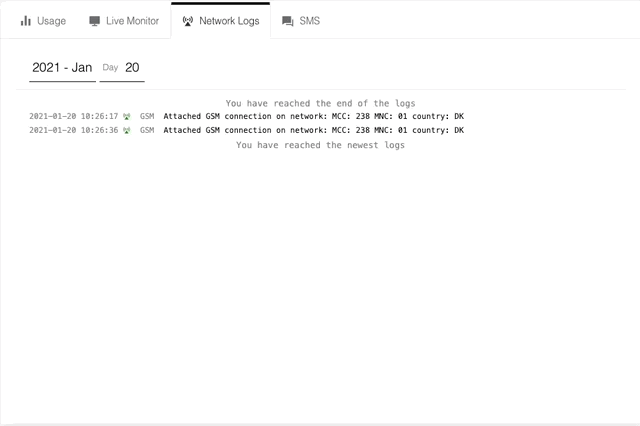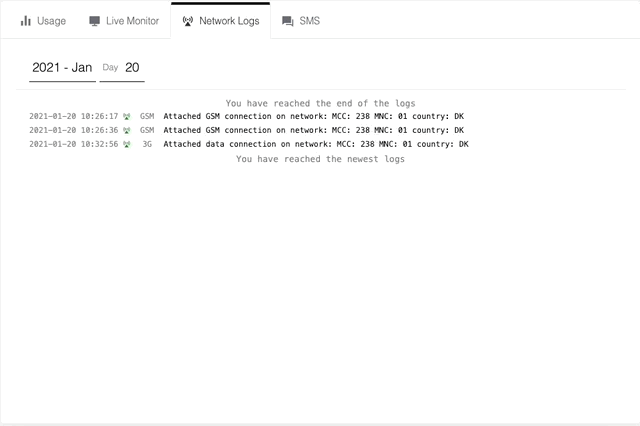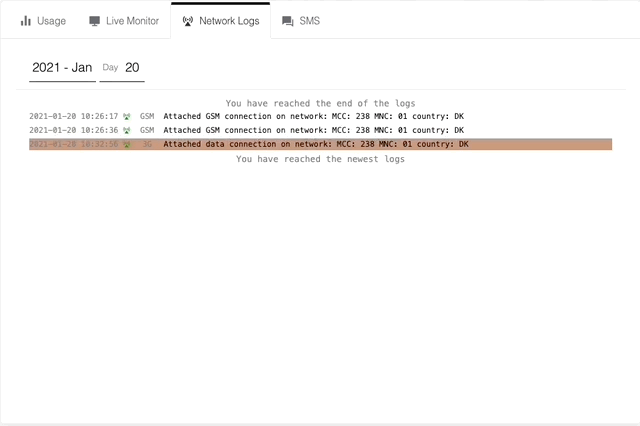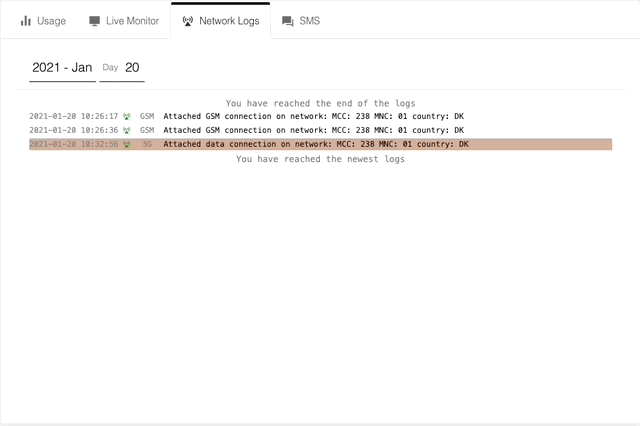
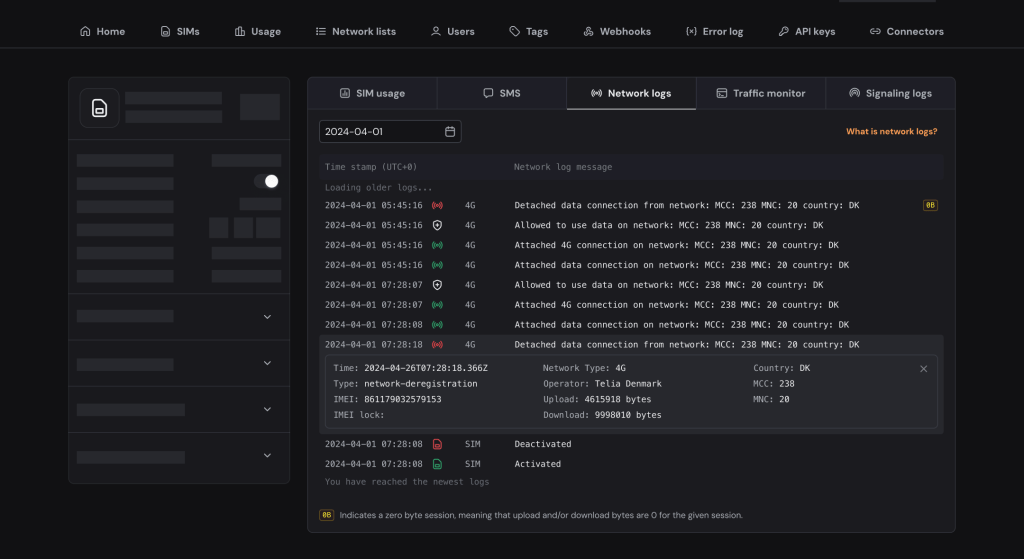
For more information on any of the network logs, you can click on the row you are interested in. This information is also available via the Onomondo API using a network-logs request.

Debugging using Network Logs
Here’s a brief example of debugging a common cellular IoT problem using Network Logs.
A forbidden networks list is part of the standards of telecom standards but can cause unwanted consequences.
For example, if the device was turned on while the SIM was deactivated, no network logs are produced but can affect future performance of the device.

Try activating the SIM again and testing again. If there are no issues you should see the device establish a connection next time it tries to connect to our network.

If you still don’t see any new network logs even though the device has tried to connect again, the device may have written all networks into the Forbidden network (FPLMN) list and will need to be cleared.
Networks are added to FPLMN list when they are not on the network list. This is to save time and energy by preventing the device to constantly try and attempt a network that has already been denied.
However, if the network list is changed to include the network, it still may not connect to the network, if it was previously been denied.

And that’s it. we hope this brief example shows you the value of Network Logs and how they can shorten the time you debugging your cellular IoT devices.